Security and Credentials
Atlas Schema Monitoring is designed with the principle of minimal access in mind. The Atlas agent is designed to only require read-only access to the database schema and only requires access to system information schema tables and not user data.
Additionally, to provide further security and control, database credentials are never provided or stored in the Atlas Cloud control plane. Instead, the Atlas agent is deployed in your environment and connects to the database directly using a variety of secure methods.
Providing credentials to the Atlas Agent
To be able to monitor the database schema, the Atlas agent needs to be able to connect to the database. However, to provide an additional layer of security, the Atlas agent does not store the database credentials in the Atlas Cloud control plane. Instead, the credentials are provided to the agent at deployment time.
The Atlas Agent supports the following methods to fetch database credentials:
- Environment variables
- Cloud IAM Roles
- Secret managers

Environment variables
The simplest way to provide database credentials to the Atlas agent is to use environment variables. The agent runs as a container on the user's infrastructure. As such, users may provide custom environment variables to the agent which can be read by the agent at run-time and used as database credentials.
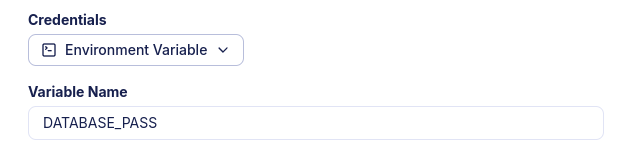
To let the agent fetch the password for a database from an environment variable, select Environment Variable in the Connection dropdown and provide the environment variables name. E.g. if the database is stored in a variable like DATABASE_PASSWORD=passw0rd you'd specify DATABASE_PASSWORD.
Cloud IAM Roles
Modern cloud providers support database authentication using IAM roles. The Atlas agent runs as a container on the user's infrastructure. As such, users may provide the agent with an IAM role that has the necessary permissions to connect to the database. The agent will then use the IAM role to authenticate with the database.
- AWS RDS Token
- GCP Cloud SQL Token (IAM Auth)
AWS RDS databases offer to obtain a short-lived token using an IAM role to authenticate against an RDS instance.
-
Enable IAM Authentication for your database. For instructions on how to do this, see the AWS documentation.
-
Create an IAM role with the "rds-db:connect" permission for the specific database and user. For instructions on how to do this, see the AWS documentation.
All you need to provide to the connection settings is the region your RDS lives in.
GCP CloudSQL offers using IAM Authentication to generate a short-lived token to use for authentication against a GCP CloudSQL database.
-
Enable IAM Authentication for your database. For instructions on how to do this, see the GCP documentation.
-
Create a database user and grant it permission to authenticate using IAM, see the GCP documentation for instructions.
All other info required to obtain a token is derived from the CloudSQL endpoint you define in the connection modal.
Secret managers
Secret managers are a secure way to store and manage sensitive information such as database credentials. The Atlas agent supports connecting to secret managers at runtime to retrieve database credentials.
- AWS Secrets Manager
- GCP Secrets Manager
AWS Secrets Manager is a secret store you can use to retrieve a secret from. This is somewhat similar to IAM
authentication, since in this case you need to have access to the secret's store, usually using IAM authentication.
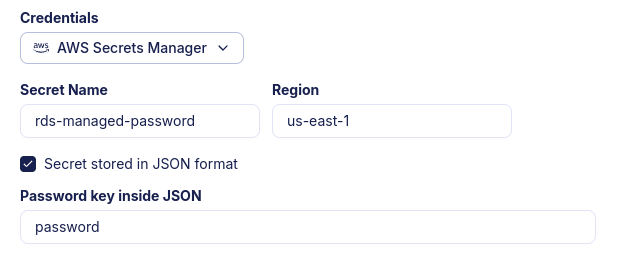
Find the secret name and region for your secret. If you need more info,
read this guide. If your secret is stored as JSON, e.g. when you
choose to let RDS handle your database password in the Secrets Manager, you can provide the path to the actual token
using a dot-notation. For example, for a secret like {"password":"my_passw0rd!"} you'd provide password as the path
to the token, and for a secret like {"nested":{"password":"my_passw0rd!"}} you'd provide nested.password.
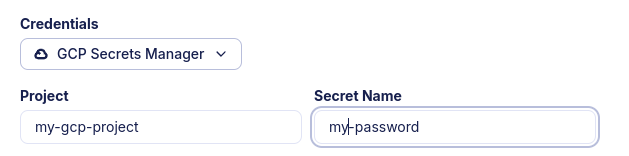
GCP Secrets Manager is a secret store you can use to retrieve a secret from. Find the project ID and secret name of your secret. If you need more info, read this guide.